THM - Diamond Model
The Diamond Model of Intrusion Analysis.pdf
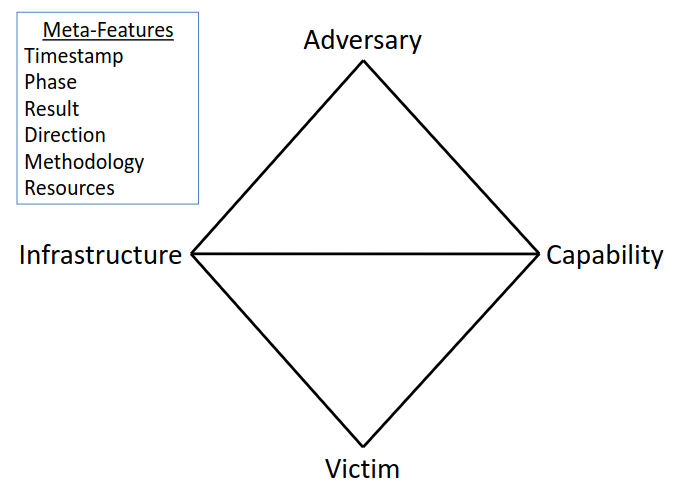
- Diamond Model of Intrusion
- A 4-pointed model of Adversary-Victim-Capability-Infrastructure that can be used to analyze any intrusion activity
- 4-points
- Adversaries
- Adversary Operator
- The hacker/person/people conducting the attack
- Adversary Customer
- The entity which stands to benefit from the attack
- Adversary Operator
- Victims
- Victim Personae
- The people
- Victim Assets
- The assets
- Victim Personae
- Capability
- All the tools, techniques, and TTPs used by the adversary
- Capability capacity
- The range of vulnerabilities and exposures that an individual capability (e.g. tool, technique, etc.) can take advantage of, regardless of the victim
- Adversary Arsenal
- The adversary's complete set of capabilities
- Infrastructure
- Type 1
- Infrastructure owned and used by the adversary
- Type 2
- Infrastructure owned by an intermediary and used by an adversary
- The intermediary may or may not be aware
- Service Providers
- Type 1
- Adversaries
- Event Meta Features
- Meta-features are not required, but can add valuable information to the model
- Six possible "meta-features" are applicable
- Timestamp
- When specific events occurred
- Phase
- e.g., which phase of the Cyber Kill Chain
- "Every malicious activity contains two or more phases which must be successfully executed in succession to achieve the desired result"
- Result
- Not always clear from an attack, but whether certain attempts were failures or successes can be helpful
- Or identifying what's uncertain
- Direction
- 6 potential values between the Adversary, Infrastructure, and Victim (including bidirectional and unknown)
- Methodology
- General classification of the intrusion event, like phishing, DDoS, etc.
- Resources
- The resources required to carry out the intrusion event
- e.g. Software, knowledge, funds, etc.
- The resources required to carry out the intrusion event
- Timestamp
- Social-political component
- The needs of the adversary; financial, social, hacktivism, espionage, etc.