MITRE ATT&CK Workshop
Workshop: MITRE ATT&CK Fundamentals - YouTube
- Understanding Pyramid of pain
- Pyramid that identifies how difficult it is for an attacker to adapt to a defender's response
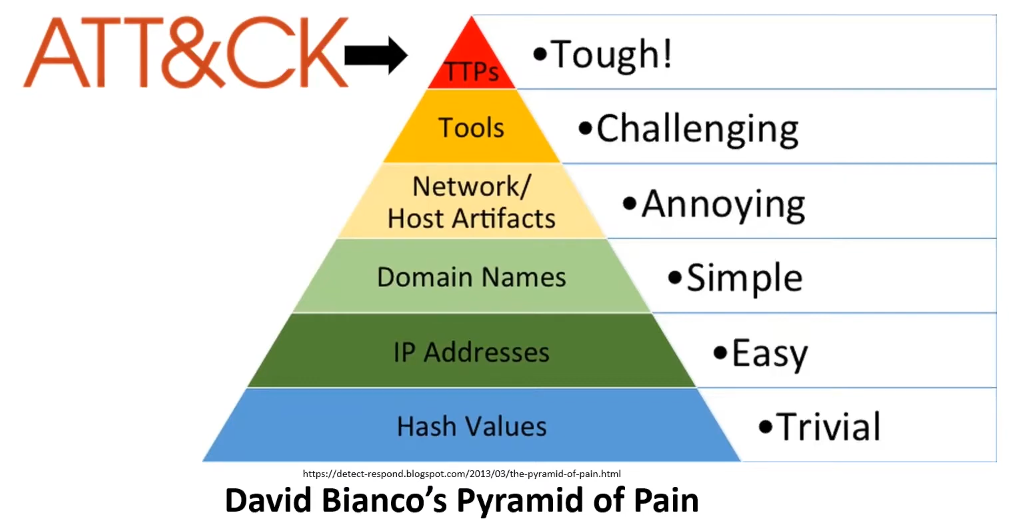
- The things we traditionally target (hashes, IPs domains, etc.) are easy or trivial for attackers to modify, but as you target higher-level elements, they become harder and harder for an attacker to adapt
- e.g., block a virus hash on your network, and the attacker just has to change a single bit for it to skate past the filter
- e.g, block a particular tool (PowerShell, etc.), and the attacker will have to figure out an entirely new vector
- The things we traditionally target (hashes, IPs domains, etc.) are easy or trivial for attackers to modify, but as you target higher-level elements, they become harder and harder for an attacker to adapt
- TTPs can be further broken down (Top down, most difficult to adapt, least difficult to adapt)
- Tactics
- Techniques
- Sub-Techniques
- Procedures
- ATT&CK
- Across the top are tactics, and each tactic contains the techniques and sub-techniques
- Each Technique/sub-technique also includes the mitigations, data sources and detections, and procedure examples
- Tactics are pretty static, but techniques change
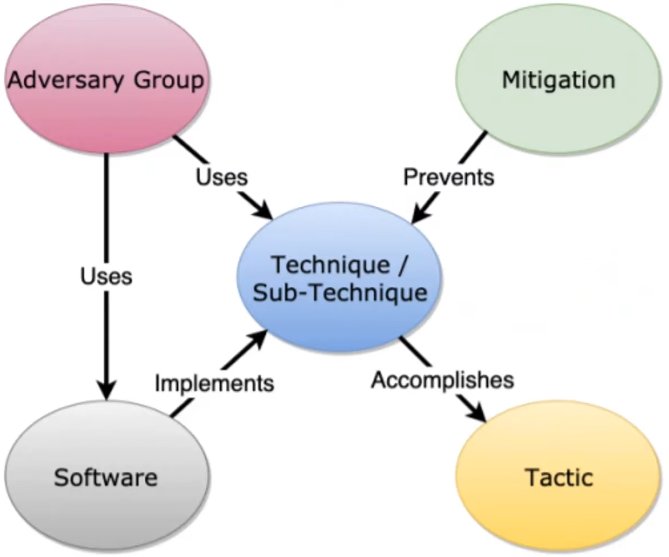
- Across the top are tactics, and each tactic contains the techniques and sub-techniques
I finished watching the video passively; need to finish my notes here.
*Actually, IIRC the rest of the video was *