NIST Frameworks and SPs Overview
When I was first getting oriented and searching the internet for help, I found a common theme that was interesting; technical people tended to over emphasize the importance of the 800-53 and undersell the importance of the CSF and RMF. One could argue this is because the CSF and RMF are significantly smaller documents and go into less detail, but I think it comes down to who we are as technicians. We get absorbed in the how, and ignore or forget about the why.
I can't help but feel like NIST also found this, and is why they made the "Govern" function central to all other funcitons.
I hope this helps fellow technical people to see the forest through the trees.
What's the recommended order for study leading to the 800-53?
Based on my research and understanding, here's my understanding on how the NIST CSF, RMF, and 800-53R5 fit together.
- The CSF is a set of guidelines and best practices designed to help organizations manage and reduce cybersecurity risks, focusing on five core functions: Identify, Protect, Detect, Respond, and Recover.
- The RMF complements the CSF by providing a systematic process for managing security and privacy risks, outlined in a series of steps.
- The 800-53 is a catalog of security and privacy controls that organizations can use to protect information systems and manage risks identified within the RMF.
Each of these documents (in particular the RMF and 800-53) are supported by Special Publications (SPs) that delve[1] into more specific topics and provide additional examples, context, and guidance to help you secure your organization.
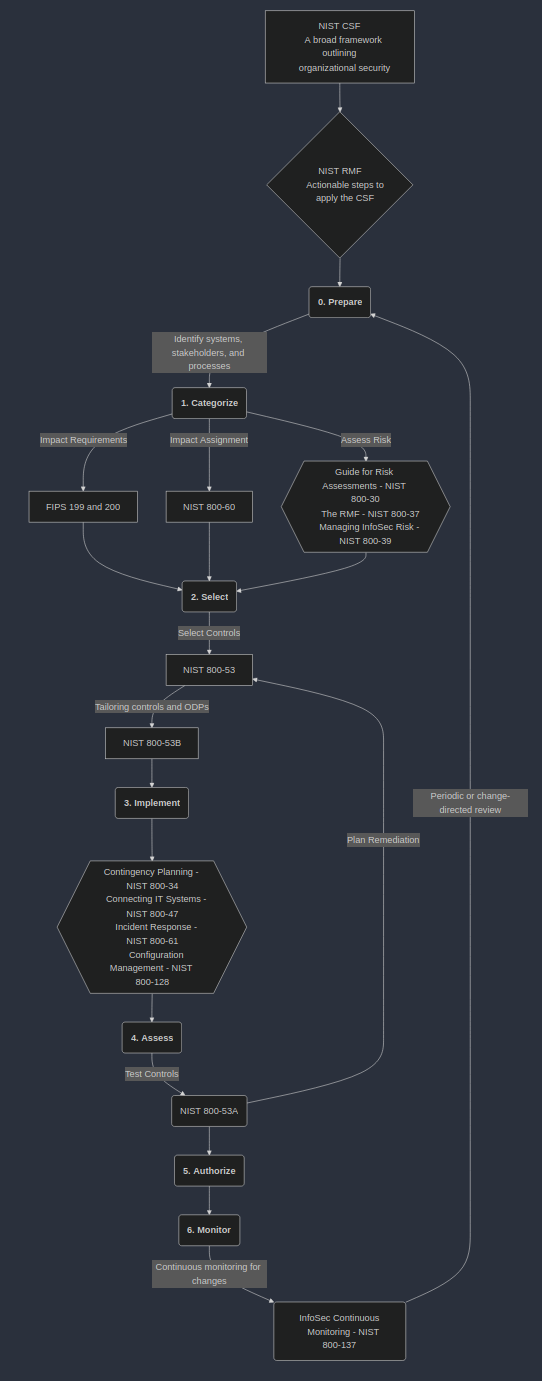
I've created a flow-chart to better illustrate this and identify how some of the SPs are used.
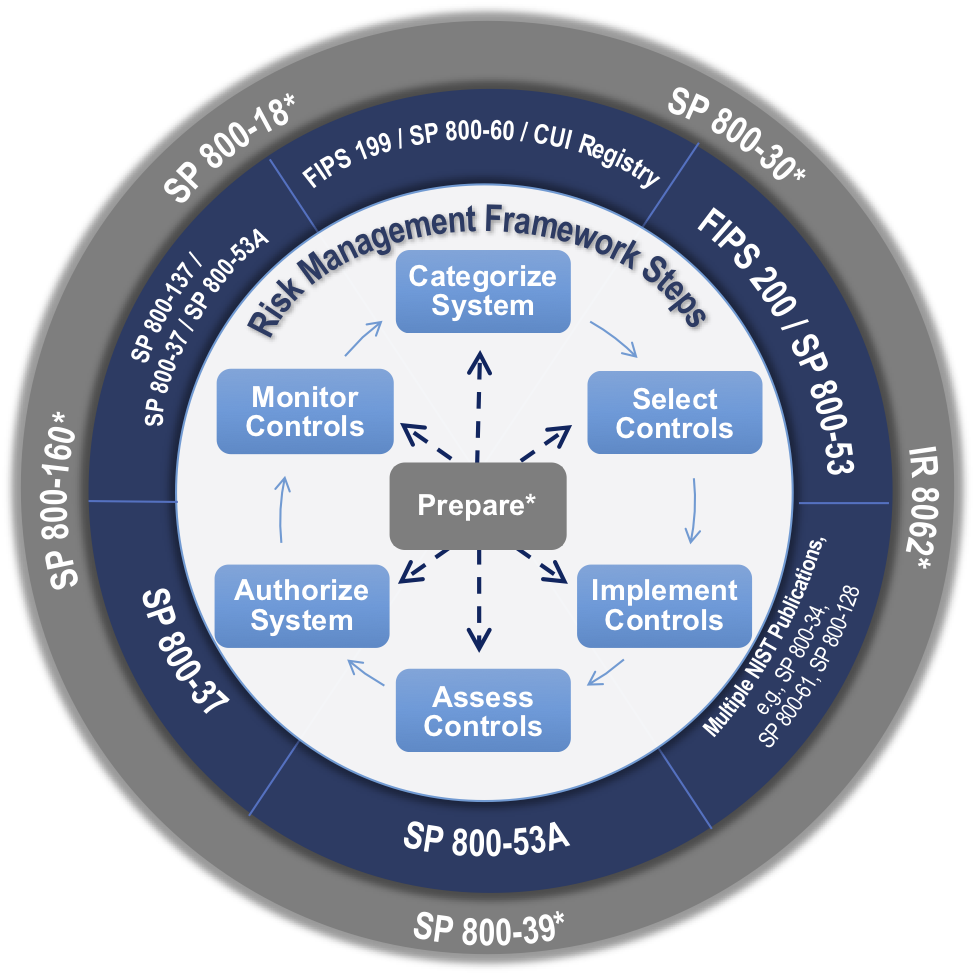
NIST also has their own chart (below), which reflects the circular nature of a strong security posture and the broad relevance of some Special Publications.
[2]
Additional Resources
Below are other sources I've used to orient myself to the NIST ecosystem of publications, with some notes on use and usefulness.
NIST Courses
NIST has a series of free online courses to introduce anyone to the RMF (800-37), 800-53, the 800-53A, and 800-53B, accessible here: NIST RMF Online Introductory Courses | CSRC
The complete courses are 6 hours in length (3 for the RMF and 3 total for the 800-53, 53A, and 53B). The courses use cookies to track progress through the slides. You're not allowed to skip forward and can't adjust the speed, which is not ideal,[3] but I guess it's better than creating an account.[4]
RiskOptics
This guide (Complete Guide to the NIST Cybersecurity Framework — RiskOptics) provides a thorough introduction to the NIST Cybersecurity Framework and how it interrelates.
ChatGPT
The list below was generated by ChatGPT, and it feels like it front loads a lot, according to the Gerald Auger video.
- NIST CSF
- Purpose: The CSF provides a high-level overview of cybersecurity concepts and outlines six core functions: Govern, Identify, Protect, Detect, Respond, and Recover. Understanding the CSF helps grasp the broader objectives of cybersecurity practices that SP 800-53 aims to support with specific controls.
- Relevance: It sets the stage for understanding the risk-based approach to selecting and implementing the appropriate controls detailed in SP 800-53.
- NIST SP 800-37 - RMF
- Purpose: SP 800-37 guides the implementation of the RMF and explains how to integrate security and risk management activities into the system development life cycle.
- Relevance: SP 800-53 is used within the RMF as the catalog of controls for organizations to implement based on their specific risk assessments. Understanding the RMF is crucial for knowing how and why specific controls from SP 800-53 are selected.
- NIST SP 800-39 - Managing Information Security Risk
4. Purpose: This document provides a structured approach to managing risk at the organizational, mission/business process, and information system levels.
5. Relevance: It helps understand the broader context of organizational risk management, within which SP 800-53 controls are applied. - NIST 800-30 - Guide for Conducting Risk Assessments
- Purpose: SP 800-30 provides detailed instructions on conducting risk assessments, which are crucial for identifying threats, vulnerabilities, and impacts.
- Relevance: Knowing how to assess risk is essential for appropriately applying and tailoring the controls in SP 800-53 to an organization’s specific needs.
- NIST 800-53A - Assessing Security and Privacy Controls
- Purpose: This publication serves as a companion document to SP 800-53, focusing on assessing the effectiveness of the implemented controls.
- Relevance: Understanding the assessment process helps ensure that the controls detailed in SP 800-53 are not only implemented but are also effective and functioning as intended.
- NIST SP 800-53
Or "dive" if "delve" is too arcane a word for you. ↩︎
Risk Management Framework (RMF) Overview - FISMA Implementation Project | CSRC ↩︎
It actually kind of sucks, because it means you can't continue progress easily on another device. ↩︎
One COULD theoretically use tools like Move Mouse and Greenshot (which gives precise mouse coordinates) to automate mouse movements and clicks to skip to the last two seconds of the video progress bar and then click "Next" to progress the slides, running it while taking a break, and then coming back later to peruse the slides and lectures at your leisure.[4] ↩︎
Not discussed in Gerald's video, but detailed here for reference ↩︎