BHIS-SOCC-lab-DeepBlueCLI
LAB: DeepBlueCLI
In this lab, we're using DeepBlueCLI to investigate Event Logs and search for patterns.
DeepBlue CLI lab
It looks like this is mostly just pre-made .evtx files[1] with examples of information one would find.
This feels like event log analysis on easy-mode; you basically just run DeepBlue against the event log file, it thinks really hard, and then outputs what it finds suspicious. However, some of the log files don't feel particularly helpful in demonstrating the power of the tool.
- Access the tool
- Inspect the Event Log Files for suspicious events
.\DeepBlue.ps1 .\evtx\new-user-security.evtx- What do we find?
- The user named named
-(just a dash) added to the Administrator group - New user
IEUseris created - Both user accounts have the same SID
- The output from DeepBlue is much cleaner than the information what we see in Event Viewer, which is really neat.
- The user named named
- I think this is a weird example to demonstrate the tool
- There are only 4 events total in the EVTX file total[4], and DeepBlue identified two of them as suspicious.
- I suppose that alone is pretty cool, but I feel like having more data for it to to parse through would be more interesting.
- What do we find?
.\DeepBlue.ps1 .\evtx\password-spray.evtx- Right away, this is much cooler test.
- If we open the file in Event Viewer, we see there are 295 events that occurred over 5 minutes
- Perusing the logs, we see that almost all of the logs show user
jwrigattempting to log in to a bunch of different users and failing over and over again
- Perusing the logs, we see that almost all of the logs show user
- DeepBlue outputs a single message summarizing what's going on.
- It identifies the kind of attack (Password Spray Attack)
- It defines the attack
- It says which accounts were targeted
- It identifies the user and computer originating the login attempts
- If we open the file in Event Viewer, we see there are 295 events that occurred over 5 minutes
- Right away, this is much cooler test.
.\DeepBlue.ps1 .\evtx\smb-password-guessing-security.evtx- Again, super interesting; it analyzed all the logs and spat out two reports for a high number of logon failures for multiple accounts
- We're told how many logon failures there are and which account is related (maybe)
- For the first report, it specifically calls out the Administrator as the account with failed login attempts, but the second report only gives the total number of accounts with failed logins.
- Looking at the files in Event Viewer, I noticed that everything except for the first log entry was for the administrator account
- Again, super interesting; it analyzed all the logs and spat out two reports for a high number of logon failures for multiple accounts
.\DeepBlue.ps1 .\evtx\Powershell-Invoke-Obfuscation-encoding-menu.evtx- This is where it gets really cool
- This event log contains a ton of obfuscated PowerShell, and the output is the most suspicious ones based on length and ratio of alphanumeric and common symbols to other symbols.
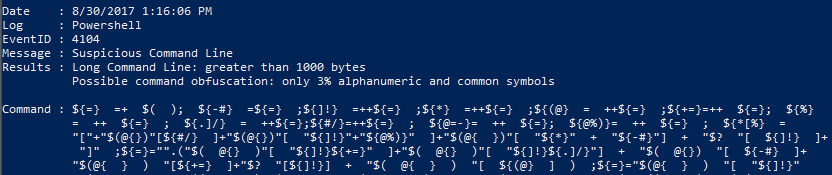
- Sample output
- We also see a range of obfuscated and Base64-encoded PowerShell commands. Yikes!
Anyway, really interesting lab, and really well crafted tool. There are a many more EVTX files to run DeepBlueCLI against and see what different kinds of activity looks like.
Additional Sources
Quick Forensics of Windows Event Logs (DeepBlueCLI) - YouTube
evtx files are exported Windows Event Log files in XML format. ↩︎
For some reason the official lab has you run Command Prompt as an admin, and then have it open PowerShell from the prompt, and I don't know why not run PowerShell as admin first... ↩︎
For more detail, check out Set-ExecutionPolicy ↩︎
We can open Event Viewer, and under "Actions" at the top right, select "Open Saved Log..." to view the logs in their natural environment. ↩︎