BHIS-SOCC-lab-FirewallLog
LAB: Server Logs Analysis
In this lab, we're analyzing logs from a Cisco ASA firewall. The output uses non-standard/Cisco standard Syslog formatting, and includes a lot of extraneous information.
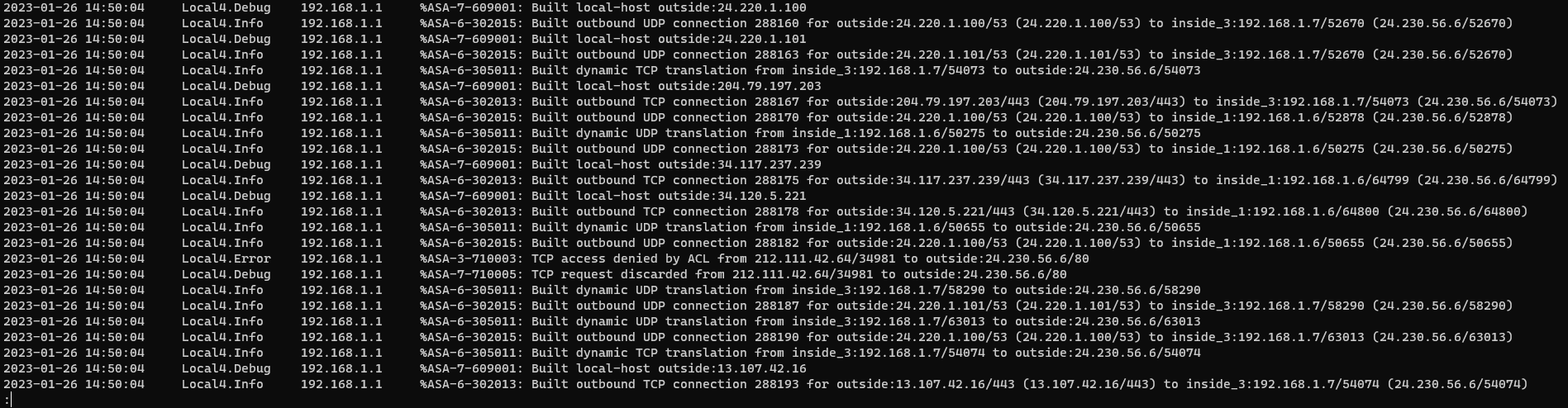
Sample of the output, unfiltered.
To start, here are the tools we're familiar with, and some that are new.
- Tools
- grep
- Only display lines with a specific string
- You can pipe
grepmultiple times to narrow down the search -v- invert-match, meaning it will EXCLUDE those results
- less
- Only show a page of results at a time
q- quitarrow up/down- scroll by linespace- page down
- cut
- Select for specific text positions in a table
-d- DELIMITER; select the delimiter-f- FIELDS; only select specific fields
- R core, or
rscript- A tool for performing math on the output
- It's kind of a whole deal, but I'll explain what happens in this use case later on
- grep
- Analyzing the logs
- Who is who?
- 192.168.1.1 is the host (firewall) system
- 192.168.1.6 is the workstation we're interested in
- 24.230.56.6 is the local gateway
- Let's use that information to clear out the logs
grep 192.168.1.6 ASA-syslogs.txt | grep -v 24.230.56.6 | less- Once that's cleared out, we see LOTS of teardown packets from a couple of external IPs to just our suspicious host.
- Let's eliminate extraneous information, and narrow down our search; let's tag on the cut command
... | cut -d' ' -f 1,3-5,7-14 | less- This spread gives us the date, event, and the message
- We can use hyphens (
3-5,7-14) to include all fields in between - What we see are tons of teardowns of TCP connections, with similar looking numbers for each remote host, 18.160..174 and 13.107..38
- If we add
| grep <remote host IP> |, we see the package sizes have very minimal variance
- If we add
- In summary, here's what we see when we isolate the logs to TCP teardowns.
- 1-second durations
- packet sizes are the same
- All with a couple IP addresses
- Alarm bells should already be going off, but let's add some rscript to further analyze the output
- Let's add some math on those byte sizes:
| Rscript -e 'scan("stdin", quiet=TRUE)-> y' -e 'cat(min(y), max(y), mean(y), sd(y), var(y), sep="\n")'- Let's break it down:
Rscript- This is just the rscript command
-e 'scan("stdin", quiet=TRUE)-> y'- The first expression is in single quotes
scan("stdin", quiet=TRUE)- Scans the standard input for information, and does not print that information to the console
-> y- The scan is sent to the
yvariable
- The scan is sent to the
- I've been a little cheeky here; the lab originally runs this in the opposite direction,
y <-scan(...)- Apparently, this is the original way to do things, but I find this less readable and intuitive, so modified it here
-e 'cat(min(y), max(y), mean(y), sd(y), var(y), sep="\n")'- This expression takes the
yvariable we just assigned and runs various operations against it- It calculates and prints the minimum, maximum, mean, standard deviation, and variance of these numbers, in that order.
catis used to concatenate[1] the output for the following functionsmin(imum),max(imum),mean,sd(standard deviation), andvar(iance) are calculated fromysep="\n"separates each calculation with a new line
- This expression takes the
- Let's break it down:
- Here's the full command for each (with some deviance from the lab for seemingly irrelevant commands)
grep 192.168.1.6 ASA-syslogs.txt | grep -v 24.230.56.6 | grep FIN | grep 18.160.185.174 | cut -d ' ' -f 14 | Rscript -e 'scan("stdin", quiet=TRUE)-> y' -e 'cat(min(y), max(y), mean(y), sd(y), var(y), sep="\n")'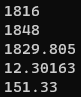
- There's very little variance or deviation; the packets are clustered really tightly around the mean of about 1829 bytes.
grep 192.168.1.6 ASA-syslogs.txt | grep -v 24.230.56.6 | grep FIN | grep 13.107.237.38 | cut -d ' ' -f 14 | Rscript -e 'scan("stdin", quiet=TRUE)-> y' -e 'cat(min(y), max(y), mean(y), sd(y), var(y), sep="\n")'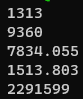
- This has a lot more deviation, but is still very concerning.
- Who is who?
- Final analysis
- Doesn't feel human
- Humans are messy and chaotic, this feels automated.
- Indicates communication with a pair of C2 servers.
- Doesn't feel human
Concatenate: link (things) together in a chain or series. ↩︎