BHIS-SOCC-lab-MemoryForensics
LAB: Memory Forensics
In this lab, we're looking at a memory dump of a compromised Windows system. To gather similar information in the wild, you can get better memory dumps by following this guide.
Lab work
- Extract the memory dump
- The first half of the lab is getting the memory dump extracted and ready to investigate.
- Running Volatility
python3 vol.py -f /mnt/c/tools/volatility_2.6_win64_standalone/memdump.vmem windows.netscanpython(3) vol.py- Runs the Volatility tool; in this lab, we're using Volatility 3, Framework 1.0.0
-f <file name>- Identifies the file being investigated, in this case,
memdump.vmem
- Identifies the file being investigated, in this case,
windows.x- The Windows module or plugin being used to analyze the files; in this particular case, the netscan module.
- Each module/plugin can significantly change the output, so I'm going to break out each module into its own deal and explain what it's doing
- It can take a few minutes for Volatility to produce an output.
- If you are running this at home (and you have the cores to spare), you can open multiple Ubuntu terminal tabs and navigate them all to the same place (after doing the initial extraction):
cd /mnt/c/IntroLabs/volatility3-1.0.0/
- If you are running this at home (and you have the cores to spare), you can open multiple Ubuntu terminal tabs and navigate them all to the same place (after doing the initial extraction):
windows.netscan- The Windows Netscan module provides information of network connections at the time of the dump
- The key ones to look for are
CLOSEDandESTABLISHED- These are connections that were open at the time of the dump, or were open recently.
- The output is long, but we can tighten it up.
- The key ones to look for are
- Trimming the search
- WARNING: An attacker could theoretically perform their activity in such a way that excluding key phrases with tools like grep might cause them to reject
- For example, the malicious application
LISTENING.exewould get culled from the output by| grep -v LISTENING - Therefore, it would be worth running multiple commands at once to cover all blindspots and efficiently go through the data
- For example, the malicious application
- The raw output is also pretty visually mangled; we can pipe to the column and less Linux commands to straighten the output and and it a little easier to read.
- WARNING: An attacker could theoretically perform their activity in such a way that excluding key phrases with tools like grep might cause them to reject
- Possible search parameters
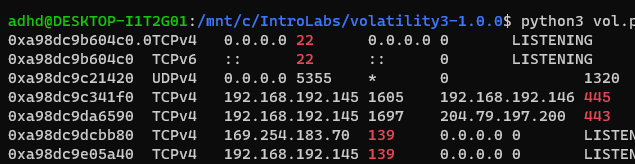
| grep -v '0.0.0.0\|::'- Removes all the listening sockets
- In this example, condenses the output from 2 pages to 1/3rd of a page
| grep 'CLOSED\|ESTABLISHED'- Just identifies any closed or open connections
| grep -w '21\|22\|23\|25\|80\|135\|139\|443\|445\|3389'- Search for the OWASP Top 10 ports listed in SOCC01 - Networking and PCAPs.
- When I first tried this command, it returned search results from all over the output, little of which was helpful
- Adding the
-wswitch searched instead of the complete "word" instead of just the string, and it cut out a ton of useless information.
- Findings
- After running our searches, using the CLOSED/ESTABLISHED grep, we get the following output
- Things we are concerned about:
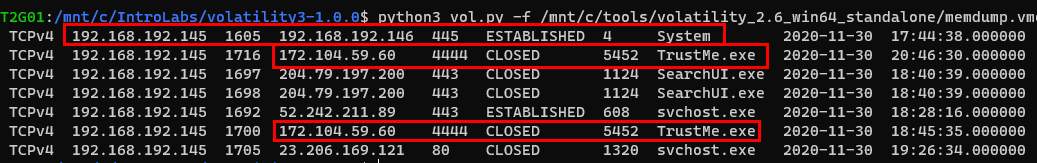
- An established
445SMB connection to another computer on the network, begun by the System process[1]- The Process ID (PID) of 4
- If we search through the output for more connections that computer, we don't find anything.
- Given that it's System, we're unlikely to find much directly linking it to itself.
- A few connections to an external IP over an unknown port 4444 from an application we don't recognize[2]
- PID is 5452
- An established
- After running our searches, using the CLOSED/ESTABLISHED grep, we get the following output
- The Windows Netscan module provides information of network connections at the time of the dump
windows.pslist- We'll use this module to check on all running processes
- You can scroll through to find suspicious ones, but it might be better at this stage to just search for the PIDs we found earlier
- More trimming! Search for the suspicious PIDs
python3 vol.py -f /mnt/c/tools/volatility_2.6_win64_standalone/memdump.vmem windows.pslist | grep -w '4\|5452'- As we search, we could add or remove PIDs from the grep
- Findings
- From this output, we can see that the TrustMe.exe process was started in cmd.exe, and this is suspicious
- Users do not run CMD on a day-to-day basis, so that's another red flag
- As expected, not a ton on the System side, though we may find more later on.
- From this output, we can see that the TrustMe.exe process was started in cmd.exe, and this is suspicious
- We'll use this module to check on all running processes
windows.pstree- This gives us the process tree, showing all processes and their relationships to each other
- Diving into one of the CMD processes, we find it tied back to
TrustMe.exe, along with a few tagalongs 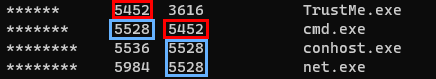
- PID on the left, Parent PID (PPID) on the right
- This information is available in
pslist, but it's not as visually apparent.
dllist --pid 5452- Shows which DLLs are associated with PID 5452
- We can see what files were loaded, when, and where from
- Findings
- TrustMe.exe was run from the Downloads folder, so that's also suspicious
- Shows which DLLs are associated with PID 5452
windows.malfind.Malfind- The "easy button" to identify malware; it checks for a specific kind of hidden/injected DLL using VAD tags
- Sadly,
column -tjust really screws up the output...
- Sadly,
- Findings
- Turns out, TrustMe.exe is bad!
- There are 4 instances with highly suspicious access to memory regions
- The "easy button" to identify malware; it checks for a specific kind of hidden/injected DLL using VAD tags
While investigating the Volatility tool, I found out that the "System" and "smss" processes will not have session IDs, because System starts before sessions are established, and SMSS is the session manager. GitHub, Volatility: pslist ↩︎
I know it's fun, but I do wish in this lab the exe was a little more normalized; like what if it was called "svchost.exe" or "WinSearchUI.exe" or something like that? Feels more realistic, and you're less likely to automatically count it as suspicious because it has a goofy name. ↩︎